How to Fix Web Application Proxy and AD FS Certificate Issues (Error Code 0x8007520C)
by
Ulison Souza
I recently moved my lab environment from one storage to another, and after moving the files and re-configuring the Hyper-V VMs, I received the following error from my Web Application Proxy (WAP):
The operation stopped due to an unknown general error. Error code 0x8007520c
For some reason I was unable to the Fastvue Reporter website that I previously published on this server, and access to the back end IIS server was not working.
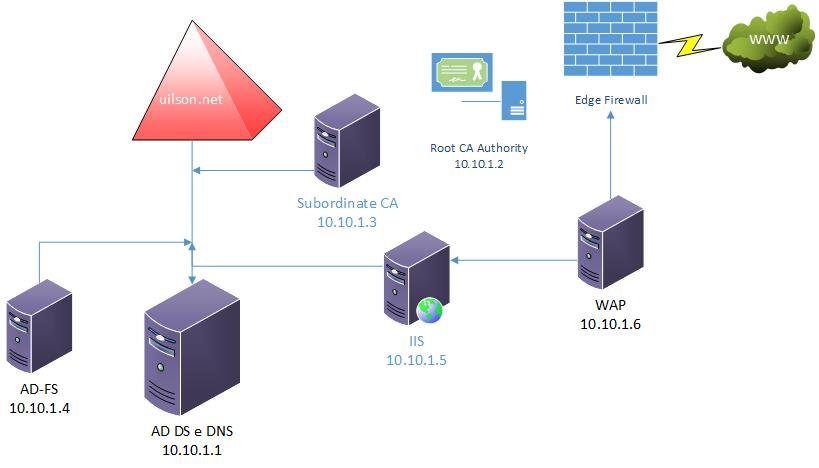
Lab Configuration
Let me show you how my lab environment is configured:
My domain "uilson.net" contains the following servers:
- AD DS and DNS – labdc.uilson.net – 10.10.1.1
- Root CA Authority – labrootca (stand alone server) – 10.10.1.2
- Subordinate CA – labsubca.uilson.net – 10.10.1.3
- AD Federation Services – labadfs.uilson.net – 10.10.1.4
- IIS / CRL-CDP-AIA / Application Server – labiis.uilson.net – 10.10.1.5
- Web Application Proxy (WAP) – labwap.uilson.net – 10.10.1.6
The labiis server hosts a non-claims application which receives pre-authentication from labadfs using my AD DS account to log in. Requests pass through labwap and then to labadfs for authorization. The user receives the AD FS authentication page requesting their AD DS credentials which forwards them to the IIS server (labiis).
Did you know: Fastvue Reporter also runs on IIS and produces clean, simple, web usage reports using data from your firewall that you can confidently send to department managers and HR team.
Event Log Troubleshooting
When trying reach the web application, access was completely down. When looking at the Event Viewer on lapwap I noticed the following event:
Unable to retrieve proxy configuration data from the Federation Service.
The error says that the WAP was unable to retrieve the configuration from the AD FS Server. I therefore logged onto the AD FS Server and discovered the following event:
The federation server proxy was not able to authenticate to the Federation Service
The AD FS Server says it's not possible for WAP to authenticate, and that there is something wrong with the certificate between both servers.
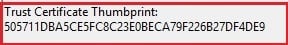
Comparing Certificate Thumbprints
When comparing the certificate thumbprint provided by the WAP Server event with the one used by the AD FS certificate, I noticed they were completely different:
If you look at all certificate thumbprints, you won't find any starting with "50571.." mentioned in the WAP server event.
Re-establishing Trust Between WAP and AD FS
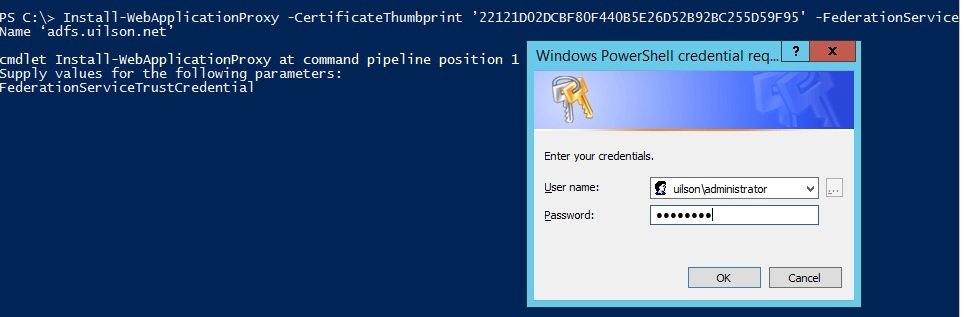
After some research, I decided to do exactly what AD FS Event ID 276 says to do: Run the Install-WebApplication Proxy cmdlet on the WAP server to re-establish trust between AD FS and WAP:
Install-WebApplicationProxy -CertificateThumbprint ’22121D02DCBF80F440B5E26D52B92BC255D59F95' -FederationServiceName ‘adfs.uilson.net’
The command above re-installs the correct certificate on the WAP Server. Note that I'm using the correct certificate thumbprint (starting with 22121…):
You need to provide your credentials in order to execute the cmdlet.
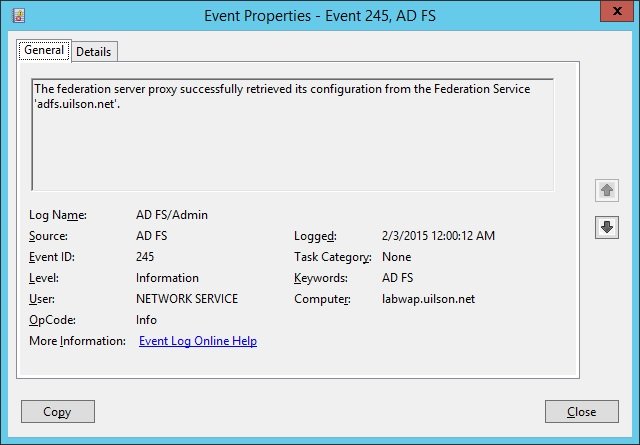
After running this cmdlet, the WAP server came back online and the configuration could be successfully retrieved from AD FS.
I could successfully view the published web applications and access to the IIS back end server was restored:
Reason For The Trust Issue Between WAP and AD FS
Once everything was working, I was curious to know why the error occurred in the first place. My Microsoft WAP/AD FS Program Managers informed me of the source of this problem:
The proxy trust certificate is a rolling certificate valid for 2 weeks and periodically updated. This is stored in an internal, protected store so you won’t see it in any of the usual certificate stores. What you see in the local machine store is the initial temporary certificate thumbprint used while the proxy trust is first being established. This explains why the WAP event log error included a strange, unknown certificate thumbprint.
If you leave your WAP server offline for more than 2 weeks, the proxy trust certificate will expire and you’ll need to re-initialise the proxy trust (which is what I did with the Install-WebApplicationProxy cmdlet).
This can also happen when you move your VM's configuration to another storage - as was my case!
You can also solve this issue by setting the following registry key to 1 on the WAP server and re-running post-install config from the Remote Management console:
HKLM\Software\Microsoft\ADFS
ProxyConfigurationStatus
- 1 (not configured)
- 2 (Web Application Proxy is configured)
I hope this helps anyone experiencing similar issues. Please leave your comments if you have any further questions!
Take the pain out of reporting on Web Usage and Network Traffic.
Fastvue Reporter produces clean, simple, web usage reports using data from your firewall that you can confidently send to department managers and HR team. In particular it can help support IT and network security teams with managing bandwith, reducing IT workload and troubleshooting with ease thanks to live alerts, dashboards and scheduled alerts. Automate reports and get the job of reporting on web usage off your desk and into the hands of people that need it. Download the 30 day free trial today!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How To Install Fastvue Reporter on your SonicWALL Analyzer or GMS Server
What everyone should know about HTTPS, SSL, TLS and Certificates