Two Factor Authentication with Sophos UTM - For Users
by

Etienne Liebetrau
The first article in this series discussed concepts and considerations for Two Factor Authentication, and why One-time Password (OTP) with soft tokens make a lot of sense. In the second article we moved through the steps required to enable Two Factor Authentication for Sophos UTM administration, using a manual process and specifying our own entropy.
When choosing a Two Factor Authentication model, you should include the cost of user enrolment as well as token management and revocation. The cost is obviously not limited to the price of the token, but also the time and administration required by both the Sophos UTM administrators and the users themselves.
This third and final article in our series on Two Factor Authentication using Sophos UTM takes you through configuring Sophos UTM for user self-enrolment of OTP, including how to revoke a token should the device be lost.
Enabling Sophos UTM's User Portal
Sophos UTM's User Portal allows your users to access everything UTM related. This includes downloading the HTTPS inspection certificate, VPN configuration, HTML5 VPN portal and self-provisioning of Two Factor Authentication tokens.
Because self-provisioning is a function of the User Portal, this feature needs to be enabled you're not already using this part of the UTM.
To enable the User Portal access for your users follow these steps.
- Navigate to Management | User Portal
- Turn on the Global Toggle Switch
- Ensure that Allow all users is checked or that the appropriate users are selected in the user list box

Specifying the users and required facilities.
Not all users may need OTP, or they may not need it for every facility. For example, you may require a user to use OTP when connecting to the SSL VPN, but you don’t mind them using just a username and password when accessing a Hotspot.
You can specify which facilities are applicable by following these steps.
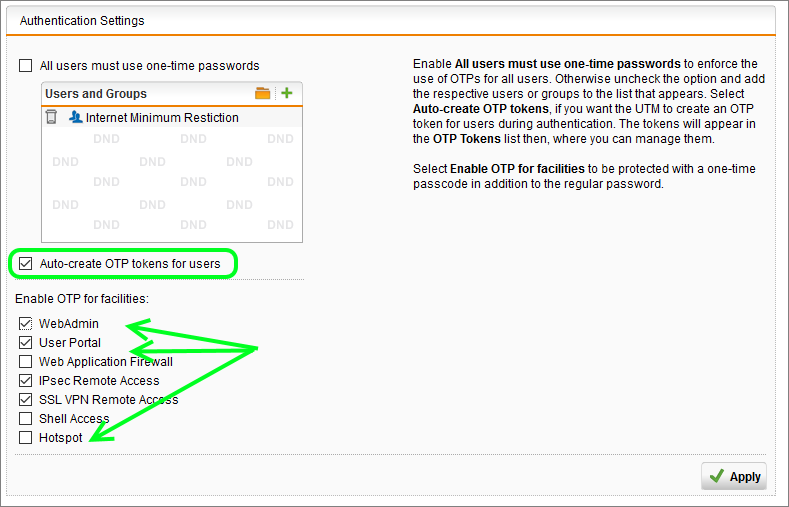
- Navigate to Definitions & Users | Authentication Services | One-time Password
- Drag the relevant user or group into the Authentication Settings Users Box
- Ensure that the box for Auto-create OTP tokens for users is checked
- Select/Deselect the appropriate facilities
- Click Apply
Sophos UTM's OTP User Self Enrolment Process
To illustrate how this works, use one of the specified users and step through the process. Please note that this process will be different, if a user (such as your admin account) already has a token associated.
- Open your browser and Browse to the User Portal. By default, it is on the same IP or name as the UTM management but on the normal HTTPS port 443 (e.g. https://yourUTM)
- Enter the normal AD username and password and then Click Login
- The User is now presented with a QR code and further instructions
- The user is instructed to start the authenticator app (Sophos Authenticator or Google Authenticator) on their smart device and scan the QR code
- Click on Proceed with login. The normal username and password login screen is presented again
- The user now enters their username and password, but this time they append the OTP to their password.
- Click Login

That’s all there is to it!
The user is only shown the QR code once and only if the token has not already been automatically created for them at a previous login attempt.
If users need to recreate their token because they plan to change phones or want to add another device, they can get the QR code from the User Portal.
It's important to note that to login to the user portal to get the QR code, they will need to login using Two Factor Authentication. If you want the tokens to be more confidential you can hide this functionality by manually enrolling users for OTP.
Token revocation and re-issue
One of the great strengths of this Two Factor Authentication method is that the token, without the user's password, is not enough to gain access. The token can be suspended by turning it off with a toggle switch (Definitions and Users | Authentication Services | One-time Passwords).
If however you need to revoke a token, it is done simply by deleting the users token next to the username on the UTM. The next time they log in with their username and password, the self-provisioning process will see that there's no token for the user, generate one and present the QR code.

You also have the Additional Codes option where you can manually or automatically add codes that will work once, and then be automatically removed from the list. This can be useful if ever a user cannot access their authenticator application, and you need to provide a code over the phone.
Conclusion
Sophos UTM's OTP self-provisioning process is very slick and helps to reduce user resistance to adopting two factor authentication.
There is also very little administrative overhead for provisioning or allocating tokens for users, once the User Portal has been enabled.
The associated cost is therefore very low from a HR perspective. You can imagine what the process would be if you had to enrol 1000 users manually, and what the turnaround time and cost would be if you needed to globally revoke and reissue all tokens.
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Two Factor Authentication with Sophos UTM – For Administrators
Two Factor Authentication with Sophos UTM - Concepts and Considerations