Sophos UTM DSL PPPoE Interface Explained
by

Etienne Liebetrau
Sophos UTM (Unified Threat Management) is a complete security product that scales from home and small office all the way up to enterprise, supporting features such as Dynamic DNS Registration, Uplink Balancing, QoS on asymmetric line speeds, and Multipath Routing.
Sophos UTM supports the use of one or more dial-up DSL connections. This article describes how to establish a PPPoE connection with your ISP through a DSL connection on the Sophos UTM.
What is PPPoE?
Point-to-Point Protocol over Ethernet (PPPoE) is a data link protocol used by most Internet Service Providers (ISP) to connect Ethernet devices over a point-to-point connection. PPP or dial-up connections can make use of DSL lines, and PPPoE allows that connection to be used by local and remote Ethernet devices.
Think of it as a connection bridge between your network and the ISP’s network. PPPoE is an encapsulation technology for ethernet frames. PPPoE can therefore be configured on Ethernet devices such as Windows or Mac OS X machines, or Ethernet routers or switches. You can configure Sophos UTM to do this for you.
Dial-up Hardware
Unfortunately, Sophos UTM devices lack the physical hardware (such as dial-up hardware or "modem" components) that handles the connection between the user and the ISP over the Public Switched Telephony (PSTN) or DSL network.
The hardware that does this needs to be configured with the correct setting such as the Multiplexing Type (normally LLC), VCI and VPI settings. This hardware is in all DSL routers or “modems”.
Since the UTM can handle the PPPoE protocol, but cannot provide the physical connection, you need a device that supplies the necessary connection hardware.
Why use Sophos UTM for DSL PPPoE?
Since most DSL routers can handle the PPPoE portion of a connection, you might be wondering why would you want to configure it on Sophos UTM. After all, you don’t have to - you can simply plug the router into the UTM. So why bother? It comes down to management, control and security.
To allow Sophos UTM to handle the PPPoE, the DSL router must be changed to bridge mode. This mean that someone connecting to the router directly would not be able to get an Internet connection. Effectively, the router becomes nothing more than a connection method.
Sophos UTM also allows you to specify additional PPPoE settings that might not be available on your router, such as setting Maximum Transmission Unit (MTU) size, VLAN tagging, and daily reconnects, which might be required by your ISP or Dynamic DNS provider. It also means that Sophos UTM is your edge router instead of your DSL modem.
Managing your connection centrally from the UTM allows you to disable unnecessary functionality on the DSL router. This provides a significant increase in security, as most manufactured routers themselves are typically not updated, patched or fixed when vulnerabilities are found.
Configuring a DSL PPPoE Interface on Sophos UTM
You will still be connecting an Ethernet cable between Sophos UTM and your DSL router. The hardware interface you use on the UTM can then be specified as the DSL (PPPoE) interface.
- Open the Interfaces & routing | Interfaces | Interfaces Tab.
- Click the + New Interface Button.
- Specify a name.
- Type: DSL (PPPoE).
- Hardware: select the relevant interface.
- Check the box for IPv4 Default GW.
- Specify Username (ISP Account).
- Specify Password (ISP Account).
- Click Save.

Configuring the DSL Router
This step will vary depending or your brand or model of router. It is not possible to cover all possible variations, but these steps are essentially uniform across the board.
- Configure the router in Bridge or Switch mode, or Enable PPPoE forwarding.
- Configuring Multiplexing, VPI and VCP settings according to telco provider.
Configuring a Netgear Router
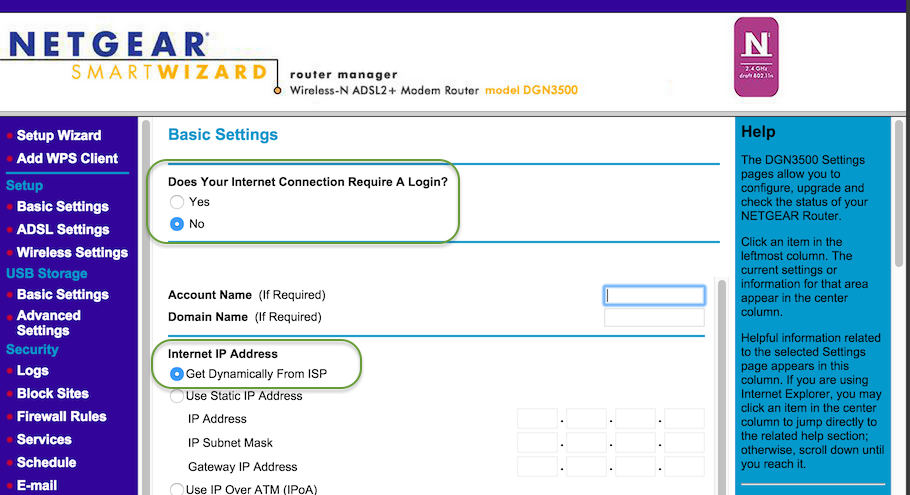
The DSL Router I am using for this example is a Netgear DGN3500. Start off by resetting the router to factory defaults, either through the management interface or by using the reset button on the back of the device.
- On the Basic Setup Screen (should be Basic WAN), set the following:
- Does your Internet Connection require a Login: No.
- Internet IP Address: Get Dynamically From ISP.
- Select the Advanced Wan Setup Screen.
- Check the box for Connect Automatically, as Required.
- Enable PPPoE Relay.
- Select the Setup ADSL settings.
- Specify Multiplexing, VPI and VCP settings.
- Optional recommended steps are to also t****urn off the WiFi and change admin username and password.
Test your DSL PPPoE Connection
You can now check Sophos UTM’s Dashboard to see if the connection comes up as expected. One additional benefit is that the UTM now knows what its public IP address is. You can see this detail by looking at the Interfaces screen.

If the connection is taking a while to come up, or if you are not sure that everything is correct, you can look at the PPPoE log for details about the connection.

Conclusion
I would personally like to see Sophos adding dial-up hardware to their SG1xx range of home and small office appliances. Until then, you have to use a connection bridge.
Configuring Sophos UTM to handle your PPPoE connection as set out in this article moves more functionality to your proper security device, and takes functionality and vulnerability away from a typically insecure device.
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Repurposing Sophos Hardware as a Multifunctional Virtual Server
Troubleshooting Sophos UTM's Remote Log Archive Feature