Repurposing Sophos Hardware as a Multifunctional Virtual Server
by

Etienne Liebetrau
I really like Sophos hardware appliances. They scale from small to large, you can convert it from Sophos XG to SG and back again, and the license is portable across the platform. They're great boxes, which got me thinking... perhaps they can be made to do more?
I just happened to have an ageing Sophos UTM SG115 in our spare parts / swap out stock and thought I'd see if it could be repurposed (or rather re-imagined) as a Virtual Server running multiple virtual devices. Wouldn't it be cool to have Sophos UTM and Sophos SUM running on the same box? Let's give it a go!
WARNING: Don't try this with your brand new firewall! It will most likely void your warranty.
Sophos = Nexcom Hardware
Okay, so this story is not really about Sophos Hardware, and this is why: Sophos, like a lot of other vendors, do not manufacture their own hardware. They source their hardware from companies like Nexcom that specialize in industrial computing devices. In the case of the Sophos 115, it is a Nexcom DNA120.
The reason I like this platform is because it is an industrialized device, built with survivability in mind. The design is completely fanless and relies on passive cooling. Even the hard disk is an SSD. This not only boosts performance but also means there are no moving parts. The device is small and has low power consumption, it also features a high network interface count. Something that is hard to find in other small computing devices such as an Intel NUK.
Another characteristic of an industrialized device, is typically the long production runs and support. Since these devices are used in industry, the focus is more on consistency and continuity over 5 to 10 years rather than quickly turning out new models every year with new features like consumer devices.
Sophos Hardware Upgrade Options
The standard Sophos 115 ships with 1 dual core Atom 1.74Ghz CPU. Significant is the fact that it supports virtualization, and that means you can make use of a type 2 hypervisor like Hyper-V or KVM. Like most other industrial or even compact devices, the CPU is soldered onto the motherboard so you can’t upgrade or do anything with this other than enabling virtualization support in the BIOS.
The standard RAM that ships is 4GB PC3-12800. There is only a single DIMM slot on the device but the hardware supports up to 8GB. So swapping it out for a bigger DIMM doubles your RAM. Easy!
The standard SSD Transcend drive that ships with the unit is a 32GB device. Depending on how you are re-purposing the device this may actually be enough for you. In my case, I swapped it out for a 256 GB unit.
Big CPU numbers make for great advertising spec sheets but generally, makes very little difference in the overall performance of a system like this. Far more important is RAM and storage performance. By swapping two "over the counter" components we have significantly boosted the capability of the device.
Building the Hypervisor
I am a pretty big fan of Microsoft Hyper-V. It is a great hypervisor that runs on almost anything. If you license Microsoft Server 2016, you get a VM license for free giving you a hypervisor and a Windows box for the same price. If, however you only want to run some Linux instance you can make use of Microsoft Hyper-V server which is free.
Before you start, you'll need to enter the BIOS and enable virtualization support from the CPU menu.
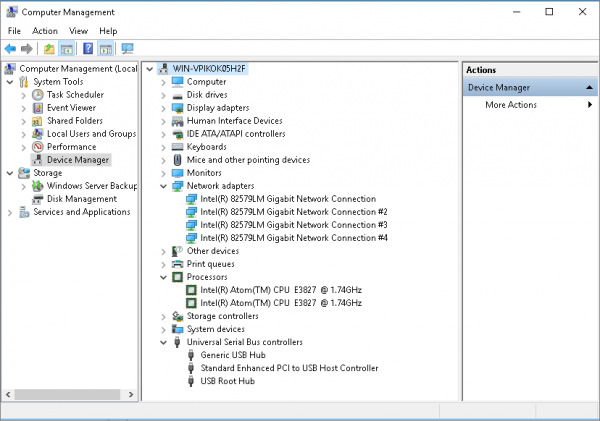
I built the device with Windows Server 2016 Standard and everything installed perfectly from the USB install drive. The only component not supported out of the box was the network interfaces. The spec sheet told me it is a 4 port Intel i227 unit, which required a separate driver download from Intel, and then I could specify the driver manually. There is no direct listing for i227 but using the Intel ® 82579LM Gigabit Network drives seems to work perfectly.
Once you have the host OS installed you can enable the Hyper-V role in Server Manager.
Next, I set up the virtual switches. This is where this little unit shows its value. You are able to specify 4 external virtual switches each tied to a physical external connector. Each virtual switch can also contain multiple VLANs.
I configure the LAN and WAN interfaces to correspond to the label interfaces on the device. I then repurposed the DMZ and HA interfaces as the second and third dedicated interfaces for the LAN but on different VLANs.
I configured three virtual switches:
- LAN or Internal
- WAN or External or Public
- SUM Management
The last interface I bind to the host without sharing it with a virtual switch. This is for Hyper-V Management.
Building the Virtual Machines
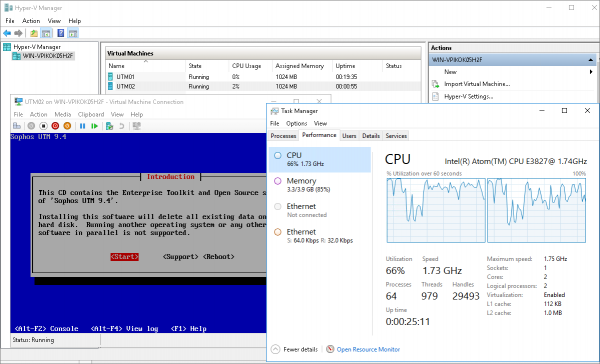
Now that everything is prepped, we can start building the virtual machines. I set up two VMs with the following specs:
- Sophos UTM Virtual 2 x CPU 4 GB RAM 32GB Storages and 2 x NIC (LAN and WAN)
- Sophos UTM Manager 1 x CPU 2 GB RAM 32 GB Storage and 1 x NIC (SUM Management)
The host is then left with 2 GB RAM and 192 GB of storage. This is plenty to run two small VMs. You could even ignore best practice and make use of the host operating system as say a local file share, or perhaps install Fastvue Sophos Reporter.
The device now runs three operating systems. The Sophos UTM firewall and Proxy, a SUM to manage this and other Sophos UTM devices, as well as a full Windows Server. Each with their own dedicated network interfaces.
We have turned a single purpose device into a three purpose device!
Practical Application
This example build was a proof of concept to show that we can repurpose a piece of hardware that was in our parts bin and swap out stock.
Imagine for instance that you need a hardy Windows or Linux Server for an industrial location. This proof of concept shows that you can get creative and do more than simply create a single purpose device.
Larger hardware units with more compute capacity and network interfaces might be more suitable for this multi-purpose design, but it is nice to know that even baby brother can join in if he has to!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Sophos UTM DSL PPPoE Interface Explained
Troubleshooting Sophos UTM's Remote Log Archive Feature