Create Real-time Alerts for WannaCry Ransomware Infected Machines
by

Scott Glew
The WannaCry Ransomware infection is currently causing havoc around the globe. Fortunately there are security patches available from Microsoft that fix the underlying security hole in SMB that the ransomware exploits. However, it is a good idea to keep an eye on any machines on your network that are or were infected.
With Fastvue Reporter for SonicWall, you can create a simple alert to receive instant notifications when machines on your network make requests to the domains that WannaCry accesses before installing (the kill switch domains that have since been registered to stop the malware spreading).
The first and second variations of WannaCry ransomware access the following domains respectively:
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
To create an alert for the WannaCry kill switch domains:
-
In Fastvue Reporter, go to Settings | Alerts and click Add Alert
-
Name the alert WannaCry Infection and click OK.
-
In the Alert Criteria section, enter the criteria: Site Domain 'Equal to' iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com AND Site Domain 'Equal to' ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com
-
In the Alert Properties section, set the Alert Key to User to create a unique alert for each user on your network (Note, if the traffic is not authenticated with your SonicWall, then the User will be the Host Name of the machine. If Fastvue Reporter has been unable to resolve the Host Name, the user will be the Source IP of the machine.
-
In the Alert Evidence section, add the columns, Source IP, Source Host, User and Action (and any other field you would like to see about WannaCry ransomware events).
-
In the Alert Notification section, enter the email addresses you would like to send notifications to when a WannaCry ransomware infection is discovered.
-
Click Save Alert, then toggle the new WannaCry Infection Alert to On
Viewing and Receiving WannaCry Ransomware Alerts
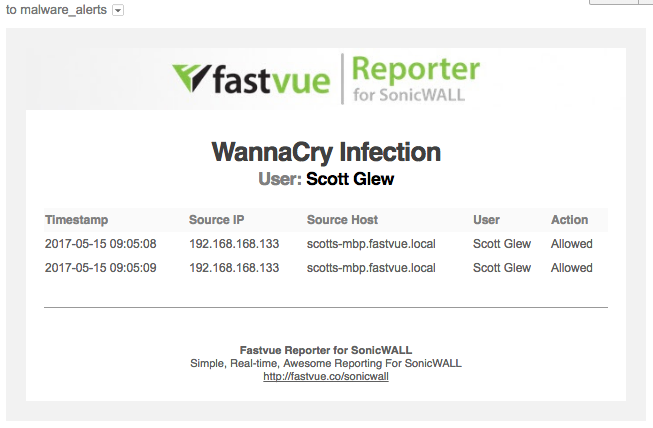
Now that the alert has been configured, you will receive alerts alerts to the email address specified, and you can also view these alerts on the Alerts tab in Fastvue Reporter for SonicWall.
WannaCry Infection Alerts in Fastvue Reporter
WannaCry Infection Alerts by Email
Limitations
Obviously, these alerts do not block the infection in anyway. They only alert on machines accessing the publicized domains that the first and second variations of WannaCry Ransomware access.
WannaCry Ransomware uses these (previously unregistered) domains to decide whether to install or not in an effort to hinder researchers running the malware in a sandboxed environment to find out how the malware works. Since these domains have been registered (first variation by @MalwareTechBlog and the second by Matt Suiche), these variations have slowed their infection rate.
However, there is already a new variation that does not make any requests to a kill switch domain, which the above alert will not pick up on. So please make sure all your machines are patched, and legacy Operating Systems are updated. See Microsoft's Customer Guidance for WannaCrypt Attacks.
Whatever you do, do not block these domains on your SonicWall. If necessary, ensure they are whitelisted. The WannaCry Ransomware will go ahead with its installation if it cannot access these domains. Also make sure you are running SonicWall's Gateway Security Services to be automatically protected (see SonicWall Protects Customers from the Latest Massive WannaCry Ransomware Attack).
Running Reports on WannaCry Infections
In addition to creating alerts to detect WannaCry Ransomware Infections in real time, you can also use Fastvue Reporter for SonicWall to run reports on historical data to find machines that have previously accessed these domain. For more information, see my new article on reporting on WannaCry Ransomware infected machines.
Good luck!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Create Real-time Alerts for WannaCry Ransomware Infected Machines (Sophos)
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)