Remote Working: 8 Tips for IT Security Teams
by

Scott Glew
Thanks to Coronavirus (COVID-19), already overstretched IT security teams worldwide have a new priority. How do IT security teams enable the entire workforce to work remotely from home while keeping the organization's network and data safe and secure? Whilst our Fastvue Reporter software helps to support IT and network security teams in the workplace, it's a different challenge for businesses with employees now increasingly working from home.
Unfortunately, Cybercriminals are not taking a break due to the Coronavirus. In fact, they're utilizing this opportunity to ramp up their operations. It's now easier than ever to get someone to click a link in an email or in social media if it looks like a legitimate piece of communication about COVID-19. In an office environment, these phishing attempts will be detected by the office firewall or spam filter. But for Work From Home (WFH) employees, all bets are off.
So, what should IT security teams be thinking about and communicating when they enable staff to work from home?
- Update and patch remote devices
- Encrypt data on remote devices
- Insist on basic home network security
- Provide a secure VPN connection
- Enforce web filtering
- Clear password policy and insist on multi-factor authentication
- Monitor and report on remote traffic
- Make it easy to report security issues
1. Update and patch remote devices
A majority of malware targets out of date, unpatched operating systems and applications.
Turn on automatic updates
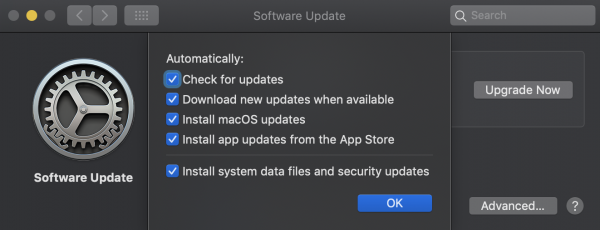
Microsoft and Apple have done a great job at staying on top of security issues and making the Operating System update process as simple as possible for end-users. Unfortunately, I think everyone has experienced the effects of a patch gone wrong, causing many people to turn off automatic updates. Get your Work From Home (WFH) staff to change this immediately. Have them check the checkbox to automatically check for and install updates.
Get remote staff to turn on Automatic Updates
Reboot regularly
Also suggest to home users to reboot their devices every day or every week, giving them the opportunity to apply patches.
Patch ALL home network devices
This doesn't just apply to the device your remote employees are using. This applies to their Xbox, their tablets, their kid's school laptops, the internet-connected fridge - any devices that connect to the home Wi-Fi can be vulnerable and infect other machines within range. You do not want these machines then connecting back to your corporate office.
Keep applications up to date
Also, think about browsers such as Chrome, Firefox and IE, applications such as Office, and new remote working tools your employees may be using such as Zoom. Make sure your employees know how to configure automatic updates across all the applications they'll be using on a day to day basis.
2. Encrypt data on remote devices
It wasn't so long ago that the biggest challenge in IT was becoming GDPR compliant. Now we're sending all our employees home into their self-managed Wi-Fi networks, and allowing them to access potentially sensitive information that we've spent the past few years protecting from this sort of access.
These devices will no longer be housed behind the swipe card security of your modern-day office building. Device theft will increase as work devices move to less secure premises in a range of socio-economic neighbourhoods.
Windows and macOS have native encryption functionality protecting data at rest, so if crooks steal the devices, they can't access your company's data.
You just have to get your remote employees to turn it on. Make sure they save their encryption passwords properly and securely (more on this later).
Get remote staff on macOS to turn on File Vault
3. Insist on basic home network security
It is unlikely that your employees have an enterprise-grade firewall protecting their home network. They probably have a simple consumer-grade router provided by their ISP.
Change the home router's default password
Make sure your remote employees have at least changed their router's password from the default. Most routers come with a simple username and password such as admin/admin. Get them to change this.
Disable WPS
Also, get your employees that are working from home to disable WPS on their home router. WPS is known to be horribly insecure and susceptible to brute force attacks.
Restrict Access to Staff Devices
When it comes to the remote employee's work device, make sure they have it secured with a strong username and password, that no one else knows - especially their kids! You don't want your corporate network becoming infected by a malicious Minecraft plugin. Reinforce that the computer should not be left unlocked as if they were in the office.
4. Provide a secure VPN connection to your corporate network
Once your devices are patched and secure, now you can start thinking about providing employees with access back to your corporate network.
Do not expose RDP
Avoid the temptation to punch a hole through your corporate firewall to allow RDP (Remote Desktop Protocol) from the public internet and instead, opt for a technology that lets you securely connect to your corporate network such as VPN.
Assume an insecure network
Keep in mind that employees may not be working from a secure/encrypted network, such as those self-isolating in hotels and using the hotel's wifi.
It's always best to lean on the side of caution and assume your remote employees are connecting from unsecured/unencrypted network. Give them access to the tools they need to connect to the corporate resources over a secure VPN.
See the Solutions section below for a range of vendors offering robust VPN solutions for remote workers.
5. Enforce web filtering
Once your remote staff have secure VPN access back to your organization's HQ, the last thing you want is for your network traffic to start resembling a home network's traffic:
Yep. This is my home network's traffic as reported by Fastvue Reporter (I have two teenage boys...)
Employees are in a different frame of mind when working from home vs working in the office. They're more relaxed, more distracted, more likely to do things that they wouldn't ordinarily do in the office, and especially with all the Coronavirus news, more likely to click links to potentially malicious websites.
To keep them protected, and your network protected, it's extremely important to apply the same web filter environment to the employees connecting over SSL VPNs as they would have when working in the office.
6. Clear password policy and insist on multi-factor authentication
It's no doubt that you're already using cloud services, perhaps for data storage and email. Think about whether you need to do anything extra around securing these services when people are not behind your corporate firewall. Almost all cloud services such as G Suite, Office 365, Slack etc provide multi-factor authentication options. Turn these features on and ensure your staff know how to get set up and log in with multi-factor authentication.
Make sure you also communicate a clear password policy that prohibits the use of the same password on more than one service. Get your employees to use a password manager such as 1password, LastPass or Keepass to avoid people being tempted to use the same password everywhere.
This is hopefully not new advice, but the stories of hacks caused by someone using the same password for their email, banking, and corporate login continue!
7. Monitor and report on remote traffic
Unfortunately, even with the best-laid plan, there are always going to be unforeseen problems. One of the biggest issues is what is becoming known as Shadow IT, where an employee or group of employees implement an IT solution to solve a specific problem they have. This can be empowering for the employee, but if left unchecked can pose security issues for your company.
For example, a team of employees may start using a free cloud service like Trello or Notion to collaborate remotely on a project. They may not realise the Trello board or Notion page has been set to 'public' while adding confidential information such as employee names and email addresses, passwords, links to internal portals and so on.
You need to stay on top of new applications and sites being uses by your remote staff so that these issues can be identified. You can then communicate with them to make sure they're aware of any potential security or data issue with using the service so they can adjust how they use the application appropriately.
Fastvue provides a number of Fastvue Reporter solutions for the major firewall security vendors. They all come with a free 30-day trial as standard. All you need to do is send the firewall's syslog data to the server you installed Fastvue Reporter on, and then access live dashboards, reports and alerts highlighting the concerns around internet usage and network security that you need to know.
Fastvue Reporter showing applications detected over the past 12 hours
8. Make it easy to report security issues
Larger organisations may already have a help desk team standing by to help with regular IT issues. But as these teams will have their work cut out for them over the coming weeks, make sure you have a separate way for your users to specifically report security issues such as an increase in phishing scams. You don't want someone with information about a critically important security risk sitting on hold for an hour waiting to get through.
Solutions
Right now, all the major security vendors are making their remote workforce capabilities such as SSL VPN and Mobile Device Management well known, with many deals and promotions. Here are some resources you may like to explore:
Sophos
- Facilitating remote working with Sophos XG Firewall
- Fastvue Sophos Reporter - Monitor and report on your remote / WFH workforce
- Sophos XG Firewall: How to configure SSL VPN remote access
- Testing Sophos XG's SSL VPN Performance – UDP or TCP?
- Setup a Sophos UTM (SG) SSL VPN In 7 Simple Steps!
SonicWall
- Work-from-Home VPN Solutions for Remote Workforces
- Fastvue Reporter for SonicWall - Monitor and report on your remote / WFH workforce
- SonicWall Remote Access VPN Clients
- SonicWall SSL VPN Setup and Configuration
Fortinet
- Fortinet Teleworker Solutions
- Fastvue Reporter for FortiGate - Monitor and report on your remote / WFH workforce
- SSL VPN for remote user cookbook
- Setup FortiClient Remote Access in FortiGate Firewall
Palo Alto:
- Securely Connect and Scale Remote Workforces with Palo Alto / Prisma
- Interested in Fastvue Reporter for Palo Alto? We have a beta almost ready to go. Register your interest here!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)
Sophos XG - How to Block Searches and URLs with Specific Keywords