How to Monitor Employee Internet Usage: Balancing Privacy with Productivity

by

Bec May
The global workplace has changed dramatically in the past five years. Enterprises globally have shifted from remote work, driven by the pandemic, to what Forbes calls the 'productivity anywhere' era, where hitherto inexperienced flexibility reigns supreme. While some organizations are mandating a return to the office, hybrid work has firmly cemented itself as the norm. According to WTW’s Global Benefit Attitudes Survey, only 34% of the workforce spend the majority of working hours in their week in the office.
This new hybrid model, unthinkable only a few years ago, presents new internal challenges. IT administrators are under pressure to manage increased bandwidth demands and ensure robust cybersecurity, while managers are under pressure from the C-Suite to maintain productivity across dispersed teams.
Employee monitoring tools have emerged as a versatile way of navigating the challenges of the modern hybrid workplace. The functionality of these solutions goes far beyond time tracking, offering innovative use cases to address bandwidth management, cybersecurity, and team productivity.
However, concerns about privacy and the intrusive nature of some 'bossware' platforms have sparked widespread debate.
Why employee internet monitoring is a must for hybrid teams
While the recent move to hybrid work was birthed from necessity, its benefits quickly became apparent. Gallup research shows that remote employees reported improved work-life balance, more efficient use of time, and burnout mitigation. However, this brave new workforce is not without its challenges. By effectively monitoring employee internet usage, organizations can address critical issues such as bandwidth management, cyber security risks, and productivity gaps.
Bandwidth management in a distributed workforce
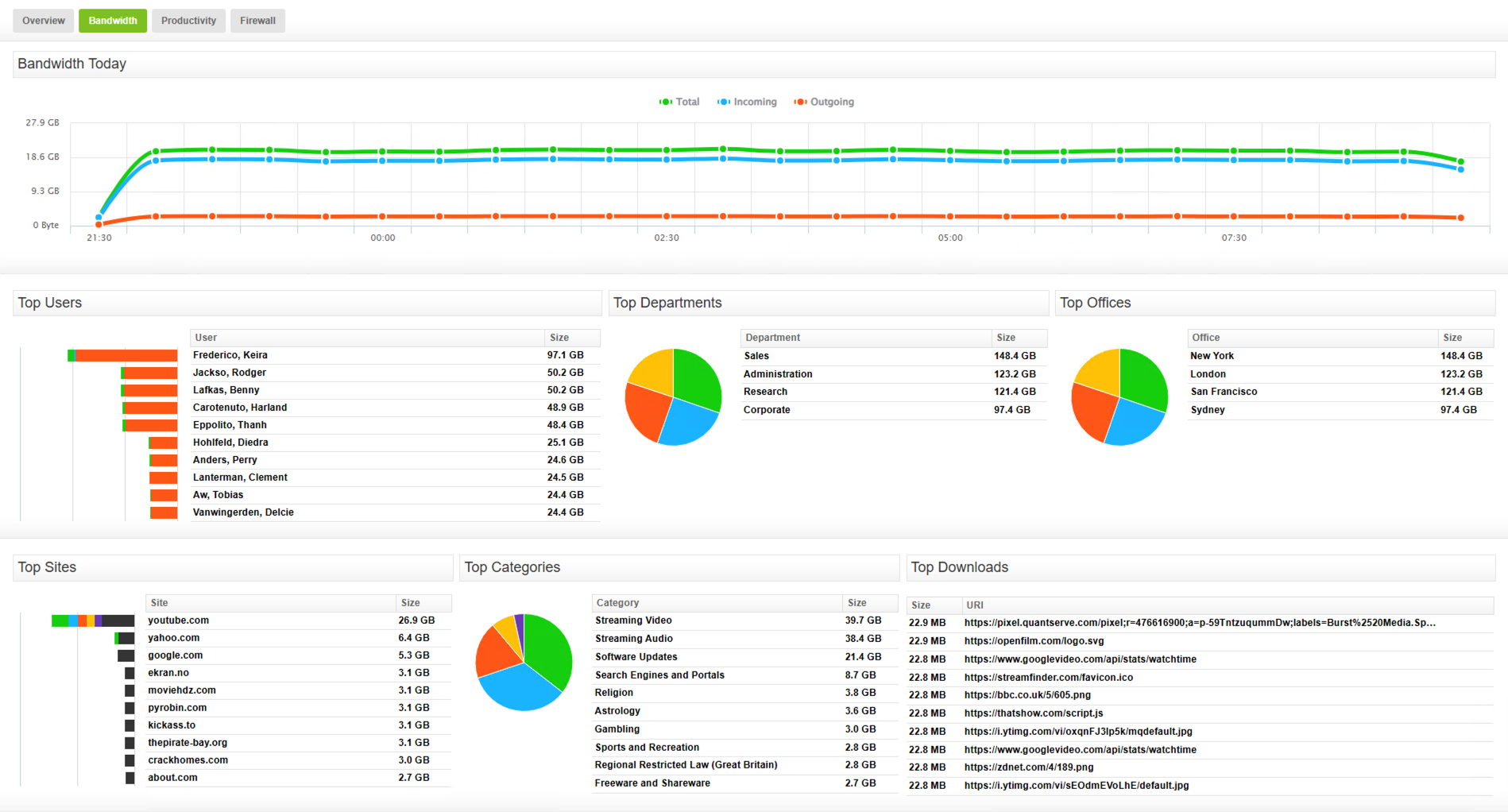
As remote work has proliferated, so has the need to manage bandwidth demands. With employees relying heavily on video conferencing, cloud-based applications, and collaboration tools, bandwidth demand can quickly spike, especially during peak hours. Non-essential activities such as streaming or downloading large non-work-related files can further strain network resources making it harder for mission-critical applications to function efficiently.
Internet monitoring gives IT teams the visibility needed to identify and manage bandwidth issues effectively. By tracking application and user behavior analytics, organizations can determine who and what is consuming the most bandwidth, prioritize essential traffic, and refine firewall policies to limit or block non-work-related websites. This ensures that key services, such as customer support systems and internal file-sharing platforms, receive the bandwidth required to perform without interruption.
Monitoring internet activity allows for proactive internet traffic management. IT teams can set alerts for bandwidth spikes and unusual network activity. With real-time insights, admins can address issues before they escalate by reallocating resources or adjusting network policies.
Safeguarding against cybersecurity threats
Mitigating phishing and malware risks
Global phishing attacks grew by a staggering 34% over the last 12 months, accounting for a significant portion of reported security incidents. Malicious actors understand that humans are often the weakest link in an organization’s cyber defenses. They dedicate their efforts to creating sophisticated and deceptive messages that exploit psychological triggers and trick users into revealing sensitive information. The stakes are high—64% of businesses reported Business Email Compromise (BEC) attacks in 2024, with an average financial loss of $150,000 per incident. Internet monitoring software can play a vital role here. Tools like Fastvue can pinpoint unusual login attempts, unauthorized file downloads, and access to malicious domains by providing real-time visibility into network activity, allowing IT teams to act swiftly before threats escalate.
VPNs and remote workers
With 92% of organizations depending on VPNs to secure remote employee computer access, Enterprise Virtual Private Networks (VPNs) are now a cornerstone of remote access. While traditional VPN/SSLVPN devices integrated into Next-Generation Firewall (NGFW)s are essential tools in this environment, their visibility on public networks and failure by management to implement proper security protocols leaves these platforms open to security risks. Many VPNs rely solely on basic username and password authentication, making them particularly vulnerable if not complemented by multifactor authentication. Additionally, poor patch management exacerbates these risks, making devices more susceptible to known vulnerabilities and exploits, including:
Zero-day vulnerabilities: Unpatched flaws in VPN software that allow attackers to infiltrate networks before fixes are deployed.
Port scanning: Hackers use tools to find and probe open VPN ports for weaknesses.
Credential theft: Phishing attacks combined with weak passwords give cybercriminals easy access to sensitive systems.
Key benefits of employee internet monitoring for VPN security
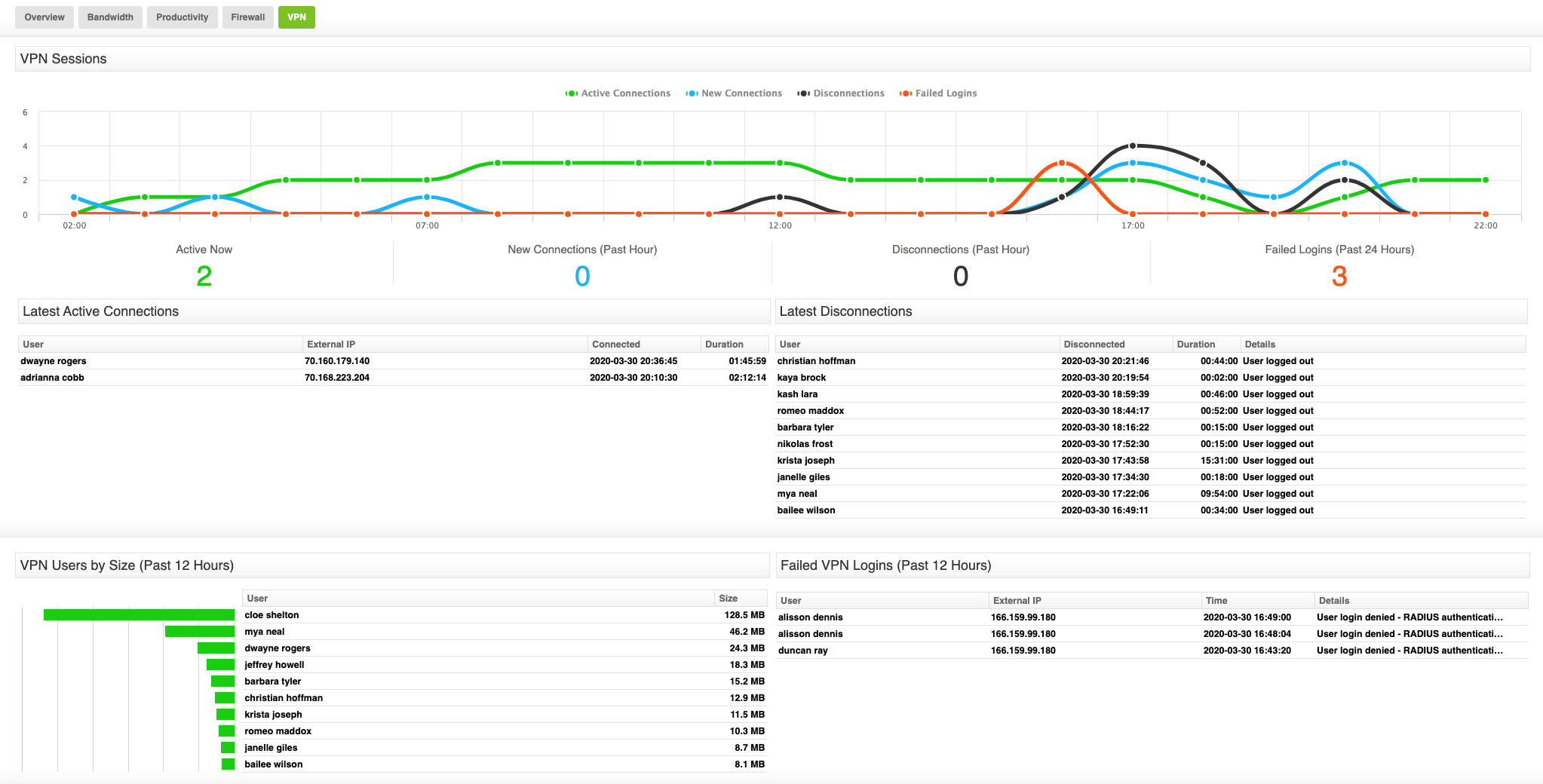
Flagging suspicious activity
Sophisticated Internet usage monitoring software can detect:
Failed login attempts that may indicate brute-force attacks
Logins from unusual and/or unauthorized locations, helping IT teams identify potential breaches
VPN disconnections that may signal unauthorized tampering or other technical issues.
Patterns that may indicate risky behavior, such as excessive file transfers
Improving visibility into VPN usage
Comprehensive network monitoring provides insights into the following:
Bandwidth consumption trends to identify overuse or misuse
The duration and frequency of VPN connections by individual users
Real-world example: How Fastvue helped a US company defend against hacking attempts with real-time alerts and reports
One of Fastvue's US customers faced persistent hacking attempts targeting their Active Directory Federation Services (ADFS) system—a critical component of their network infrastructure. By employing Fastvue Reporter, the company’s IT team was able to quickly identify and block suspicious IP addresses attempting to exploit vulnerabilities — something they were struggling to do with their firewall’s native reporting capabilities. Fastvue's real-time alerts and comprehensive internet usage reports facilitated:
Detection of unauthorized login attempts.
Tracking of malicious activity back to specific IP addresses.
Proactive strengthening of their firewall rules to prevent future attacks.
Employee monitoring for productivity and wellbeing
As hybrid work becomes the norm, and business leaders are spending less time in the same physical space as their employees, monitoring workplace productivity, employee performance, and staff wellbeing has become increasingly challenging. Without casual in-person check-ins and the ability to observe work habits directly, organizations face the risk of losing touch with their teams' day-to-day performance and mental health.
Internet monitoring tools provide a critical solution to these challenges, offering organizations the ability to track productivity metrics, including time spent on work-related tasks versus non-productive activity like scrolling social media sites. These tools can also flag indicators of potential well-being concerns, such as searches related to self-harm or excessive late-night activity, suggesting overworking and potential burnout. These real-time alerts can be set up to alert HR or other designated personnel, ensuring timely support for at-risk employees.
Furthermore, when staff are informed in advance that these systems are in place, network monitoring has been shown to significantly enhance productivity, offering tangible results to employers.
The concerns around employee monitoring software
While there are apparent benefits to monitoring your employees' internet activity, not all computer monitoring software is designed with employee privacy in mind. Some software and organizations take employee monitoring to another level, treading a fine line between reporting and surveillance.
These technologies range from innocuous to intrusive, including:
Keystroke logging software: Tracks every keystroke made on company-owned computers. While keystroke logging is often used for detecting sensitive data entry, these monitoring systems have been widely criticized for privacy invasion, with many well-publicized cases of businesses rolling this out without explicit employee permission.
Webcam monitoring software: Uses facial recognition and object detection to ensure the authorized use of sensitive systems. In extreme use cases, this employee monitoring software identifies activities like unauthorized individuals in view or prohibited behaviors such as eating, drinking, or unassigned toilet breaks(!).
Screen capturing tools: Screen capturing tools periodically take images of employees' computer screens to track their activity. These tools may pride themselves on being 'the best way to do forensic investigations', but they are not in the business of law enforcement. While they may be intended to provide transparency and track inefficiencies, these tools and how organizations handle the associated employee data can quickly traverse ethical and legal boundaries. One such company, which was outed on Reddit, displayed employee screenshots as a slideshow on a TV in the office, exposing sensitive information like salaries, social insurance numbers, and personal emails. While no doubt at the extreme end of the spectrum, the resulting legal and reputational fallout that ensued (many employees went on to sue the company) serves as a cautionary tale of how intrusive monitoring can erode trust, violate privacy, and lead to significant financial and legal consequences.
Activity timers: Monitor idle versus active work time, often used in freelance environments. These tools can misrepresent productivity if they fail to account for non-digital tasks like brainstorming or phone calls.
Website and application monitoring: Tracks the websites and applications employees use during work hours, offering a balanced way to evaluate productivity without delving into private activity.
Mouse tracking software: Measures mouse movement to infer activity levels. Like keystroke logging, this technology often draws criticism for promoting a culture of micromanagement over trust. Its implementation in many organizations has spurred the rise of tools like mouse jigglers, which artificially move cursors to simulate activity, demonstrating the pushback from employees against rigid monitoring practices.
Balancing security, transparency, privacy, and productivity: Which monitoring software is right for your team
In the US, employers are generally permitted to monitor employees on work-issued devices as long as it aligns with the best interests of the business. Some state laws mandate that employees provide consent, which is often obtained in employee contracts of internet usage policies that are skimmed over and then thrown into a drive somewhere. This means many employees are often unaware that they have consented to monitoring, leading to surprise, concern, and resentment upon discovering their activity is being tracked.
Further to this, employee monitoring tools that track workers' every move, from bathroom breaks to other household members walking through an employee's space, are shown to create high levels of anxiety and stress. The sense of being watched can create a toxic workplace environment where job satisfaction and productivity dips.
Additionally, these tools collect vast amounts of personal data, including photographs, screenshots of personal emails, and insights into private activities, raising concerns about the potential misuse or unauthorized access to sensitive information.
When selecting and implementing employee monitoring software, it's important to balance productivity, privacy, and overall workplace culture. Overly intrusive monitoring can alienate employees, while vague or poorly implemented policies can undermine their trust.
As Professor Peter Leonard of UNSW Business School explains: “There is understandable concern among employees about employers spying on their activities. There are many examples where employers are demonstrably intrusive and disrespectful in their monitoring practices.
“Some employers simply don’t understand how to implement responsible data governance practices that limit monitoring to that which is reasonable, necessary, and proportionate,” says Prof. Leonard.
So, let’s now look at some ways that companies can approach monitoring with a focus on transparency, clear goals, and ethical practices.
Transparency around monitoring practices: Build trust, not resentment
Transparency is the cornerstone of effective employee monitoring. At Fastvue, we encourage our clients to begin by openly communicating with their team about the following:
Why monitoring is necessary: Explain how monitoring links to organizational goals like improving workflow, enhancing security, and supporting well-being rather than micromanaging daily activities.
What is being monitored: Outline the scope of monitoring, such as websites visited, time spent on application applications, or network activity,
How employee data will be used: Reassure employees that collected data will be used constructively, such as for coaching or identifying resource needs, not for punitive measures.
Contextualizing employee activity
Monitoring employee activity, such as time spent on work-approved websites, can provide valuable insights, but it doesn't always tell the full story. To understand productivity more clearly, it’s important to look beyond simple metrics and consider the context of the activity. For example, employees may spend time on YouTube or other ‘social’ platforms, but that time may be spent engaging with content that is relevant to their work or professional development.
Fastvue helps to provide a clearer picture, allowing organizations to monitor exactly which YouTube videos were watched and for how long. This level of detail helps to contextualize activity, showing whether the time spent on these platforms is related to work objectives or personal browsing.
Ethical data governance: protecting privacy
Choose software that aligns with ethical data government practices to prevent overreach and ensure employee privacy. Key considerations include.
Minimal data collection: Collect only the information necessary to meet your organizational goals and avoid invasive practices like keylogging or webcam monitoring unless absolutely justified.
Secure data storage: Implement secure encryption and access controls to protect collector data from misuse or breaches
Anonymized reporting: Where possible, provide anonymous data and team-level reports to managers, reserving individual-level insights for cases with detailed oversight is necessary.
Integrating monitoring with employee development
Monitoring should support employees, not just report on them. You can use insights from monitoring software to:
Identify support needs: Highlight areas where employees might require additional training or tools to perform their roles more effectively.
Encourage healthy work habits: Monitor for signs of overwork or well-being issues such as extended hours or concerning search terms and offer timely support.
Reward outcomes: Leverage your reporting data to reinforce positive behavior and improve morale.
A better way: transparency and balanced internet monitoring
Responsible internet monitoring software offers an alternative to invasive surveillance. Tools like Fastvue Reporter provide actionable insights without resorting to intrusive tactics:
Real-time reporting: Understand productivity trends without excessive tracking.
Actionable alerts: Detect risky behaviors, such as shadow IT or unproductive browsing, without micromanaging employees.
Granular data: Provide managers with detailed reports that offer granular data, ensuring context, fairness, and accuracy in assessments while fostering trust and collaboration within teams.
Leverages Existing Data: Fastvue doesn’t log new information; it imports data already collected by your existing firewall, presenting it in clear, actionable reports and real-time alerts.
By integrating balanced monitoring practices, organizations can protect their operations while maintaining employee satisfaction and trust. The goal should be to enhance productivity and security without crossing the line into unnecessary surveillance.
Join top organizations using Fastvue Reporter
Download Fastvue Reporter now and try it free for 14 days or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn