How Employee Monitoring Can Help Detect Insider Threats

by

Bec May
Insider threats. It may sound like a Hollywood film where vigilantes take down an organization's network and save the world, but the reality is usually far less dramatic. The majority of insider threats actually stem from negligence, poor security awareness, and plain old oversight. While insider threats usually lack the drama of a big-budget film, their impact can be just as staggering, with one report finding the average cost to large companies has hit an explosive $16.2 million.
While this amount may seem unimaginable for smaller enterprises, the costs of insider threats go far beyond a mere dollar value. A single incident can irreparably damage your organization's reputation, erode customer trust, and lead to compliance violations—which can attract hefty penalties. For many businesses, the costs of an insider attack can be devastating.
This is where employee internet monitoring solutions enter the scene, acting as a vital first line of defense. By offering insights into user behavior, flagging unusual activities, and providing clear visibility into what's happening across your network, these tools enable you to identify potential threats, address vulnerabilities, and minimize the risks associated with insider threats.
But how can organizations recognize the warning signs of an insider threat? And how can the right monitoring solutions help detect suspicious activity, mitigate risks, and maintain a balance between security and employee trust? Let's explore how employee monitoring solutions can help to tackle insider threats and safeguard organizational resilience.
Who is defined as an insider?
In network security, an insider is any individual with authorized access to an organization's systems, network, and data. This includes current and former employees, contractors, vendors, and businesses who hold or have previously held privileged access.
Insiders are unique cybersecurity risks as their actions, whether intentional or unintentional, originate within an organization's trusted environment. Examples of insiders include:
Current employees: Individuals actively working within the organization.
Former employees: Those who retain access after leaving the company, either due to oversight or deliberate intent.
Contractors or vendors: External partners granted access to fulfill their role.
Business partners: Entities with shared access to collaborative systems or data
Regardless of their role and intent, insiders can pose a significant threat to an organization's security. In fact, insider threats are reportedly the cause of 60% of data breaches, underscoring the importance of understanding and addressing these vulnerabilities.
Unintentional threats and negligent insiders
Unintentional threats occur when an employee fails to follow proper IT procedures. It's often as simple as an office employee failing to log out of their account on close of business or an IT admin failing to apply a recent security patch. At this stage, they are negligent insiders, individuals whose risky behavior creates a vulnerability that has not yet been exploited by a third party. However, once an external actor exploits these credentials, the negligent insider transitions to a compromised insider, becoming an unintentional conduit for data breaches and security incidents.
A real-world example of this is the 2022 Uber data breach, which involved a tactic known as MFA fatigue. In this case, an external attacker obtained an Uber contractor's corporate password, likely via malware or the dark web. The malicious actor repeatedly attempted to sign in using these login credentials, triggering a flood of multi-factor authentication (MFA) push notifications on the contractor's device. While the contractor initially ignored the requests, the persistent barrage eventually wore them down, leading them to approve one of the notifications, unknowingly granting the attacker access to Uber's internal systems.
Once inside, the attacker exploited this access to navigate the network and steal sensitive data, including information from Uber's bounty program. The contractor was initially a negligent insider, but by failing to report the unusual activity or take precautions, they became a compromised insider, as their credentials were actively exploited to breach Uber's systems.
Intentional threats and malicious insiders
While 62% of insider threats arise from unintentional actions, such as negligence or oversight, malicious insiders—those acting with intent—continue to pose a significant risk to organizations. These individuals, often disgruntled employees, contractors, or partners, exploit their legitimate access to sensitive data for personal gain, competitive advantage, or outright sabotage. Their actions are usually carefully planned and can inflict substantial operational, financial, and reputational damage.
A malicious insider may exfiltrate sensitive data, such as trade secrets or customer information, to external drives or unauthorized cloud storage. An employee might attempt to mask this activity by renaming files or encrypting them to appear as routine transfers. Others may sabotage operations by deleting critical data, adjusting system configurations, or introducing malware, effectively paralyzing business functions. Privileged users, such as administrators, may abuse their elevated access to gain control unrelated to the role, escalating privileges over time to broaden their reach.
Large, global corporations often find themselves the target of malicious insiders, as was the case with Anthony Levandowski, a former Google executive. In 2016, Levandowski downloaded thousands of files related to Google's self-driving car program, Project Chauffer (now Waymo LLC), onto his laptop before leaving the company to work at rival Uber. Contained in these files were sensitive trade secrets that gave Uber a competitive edge in the autonomous vehicle market, which a court later valued at $1.5. million USD.
Shadow IT and insider threats: A growing concern
Shadow IT, the use of unauthorized software, devices, or cloud services by employees, represents a significant security risk. Research by cybersecurity firm Armis reveals that employees in over two-thirds of UK organizations are installing unauthorized software on work devices without IT approval. While this may be done to improve productivity or convenience, it inadvertently opens the door to insider threats and data breaches.
Shadow IT creates blind spots for IT teams, making it harder to monitor and secure organizational data. Due to the decentralization of assets, shadow data accounts for 35% of data breaches, which are associated with a 16% higher cost and longer time to identify and contain them.
Employee monitoring tools like Fastvue can give organizations the visibility needed to understand network traffic and user behavior. These tools can identify unauthorized software downloads, report on data movement to unapproved cloud services, and flag unusual patterns, including off-hour logins and access to restricted files. By offering a detailed view of network activity, monitoring solutions help IT teams detect and address Shadow IT risk early, protecting sensitive data and reducing the likelihood of insider threats.
Technical indicators of insider threats
Here are some technical indicators that you might be dealing with an insider threat and may want to start running some reports to gain further information:
Unusual data movement: This can include spikes in data downloads, employees sending internal files to personal email accounts, or using unauthorized file-sharing tools like AirDrop.
Unapproved software installation: Using unsanctioned tools that bypass security controls and create vulnerabilities.

Back doors for external access: The detection of unauthorized remote access tools such as TeamViewer or AnyDesk installed on work devices.
Abnormal login behavior: Multiple concurrent session logins at unusual times or from geographically distant locations.
File manipulation: Renaming files or using extensions that disguise content to exfiltration or sensitive data.
Modified security settings: Changes to firewall rules, antivirus configurations, or other security systems that pave the way for exploitation.
If you notice any of the above, alarm bells should start ringing. However, technical alerts don't offer the complete picture, especially when it comes to intentional threats. Driven by malicious intent, these users will generally demonstrate suspicious behavior in the lead-up to an attack.
Behavioral indicators of insider threats
Here are some behavioral indicators that may indicate suspicious activity is afoot in your organization:
Visible and audible dissatisfaction or resentment towards colleagues or leadership.
Routine violations of organizational policies.
A sudden spike in interest in projects or data outside their scope of work.
Working off-hours without justification.
Visiting URLs or YouTube videos featuring concerning content.
While these behaviors could be related to personal issues or simply having an 'off' day, when paired with critical data gleaned from employee monitoring tools, they can begin to paint a picture of employee activity that may warrant further investigation.
Insider threat management: Steps to detect and mitigate insider threats
Effectively managing insider threats requires proactive monitoring, strategic asset protection, and fostering a culture of security. At Fastvue, we encourage our customers to:
Enhance visibility with real-time monitoring
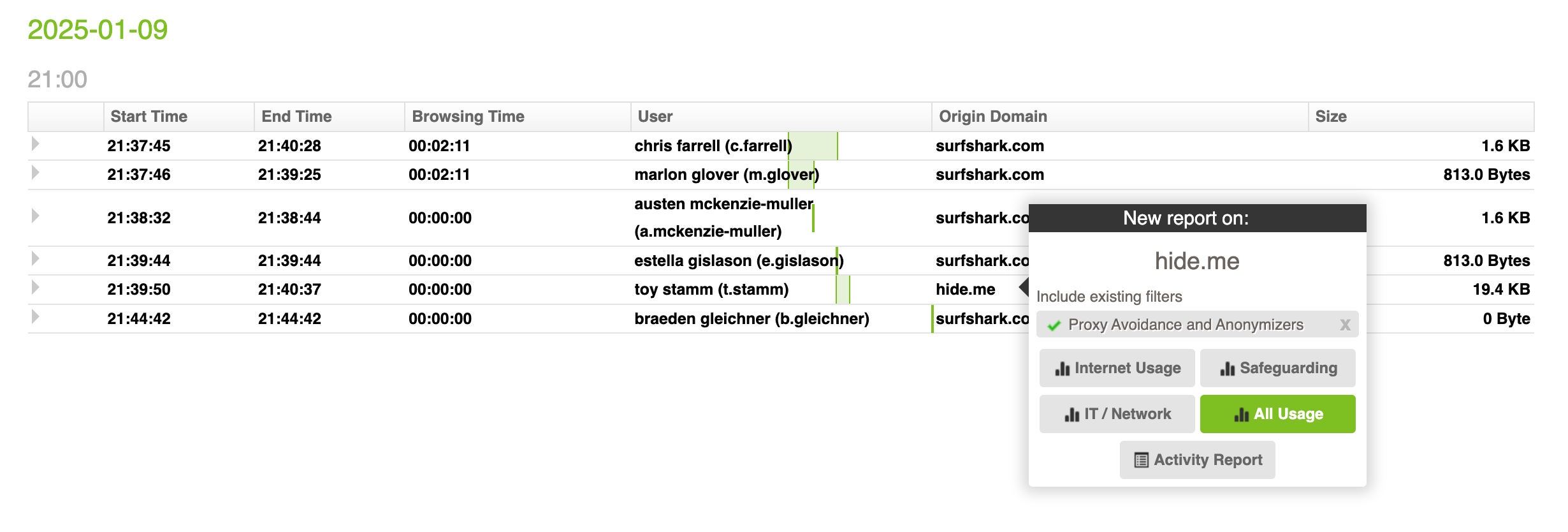
Employee monitoring software enables organizations to track employee activity and detect potential threats in real-time. By using user activity monitoring software, organizations can :
Identify unusual user behavior analytics patterns, such as abnormal login times or large data transfers.
Flag attempts to bypass security controls, such as using unauthorized software.
Detect privileged access misuse and the risk of data exfiltration
Configure real-time alerts for large downloads, uploads, and other events, enabling security teams to respond quickly and start an investigation.
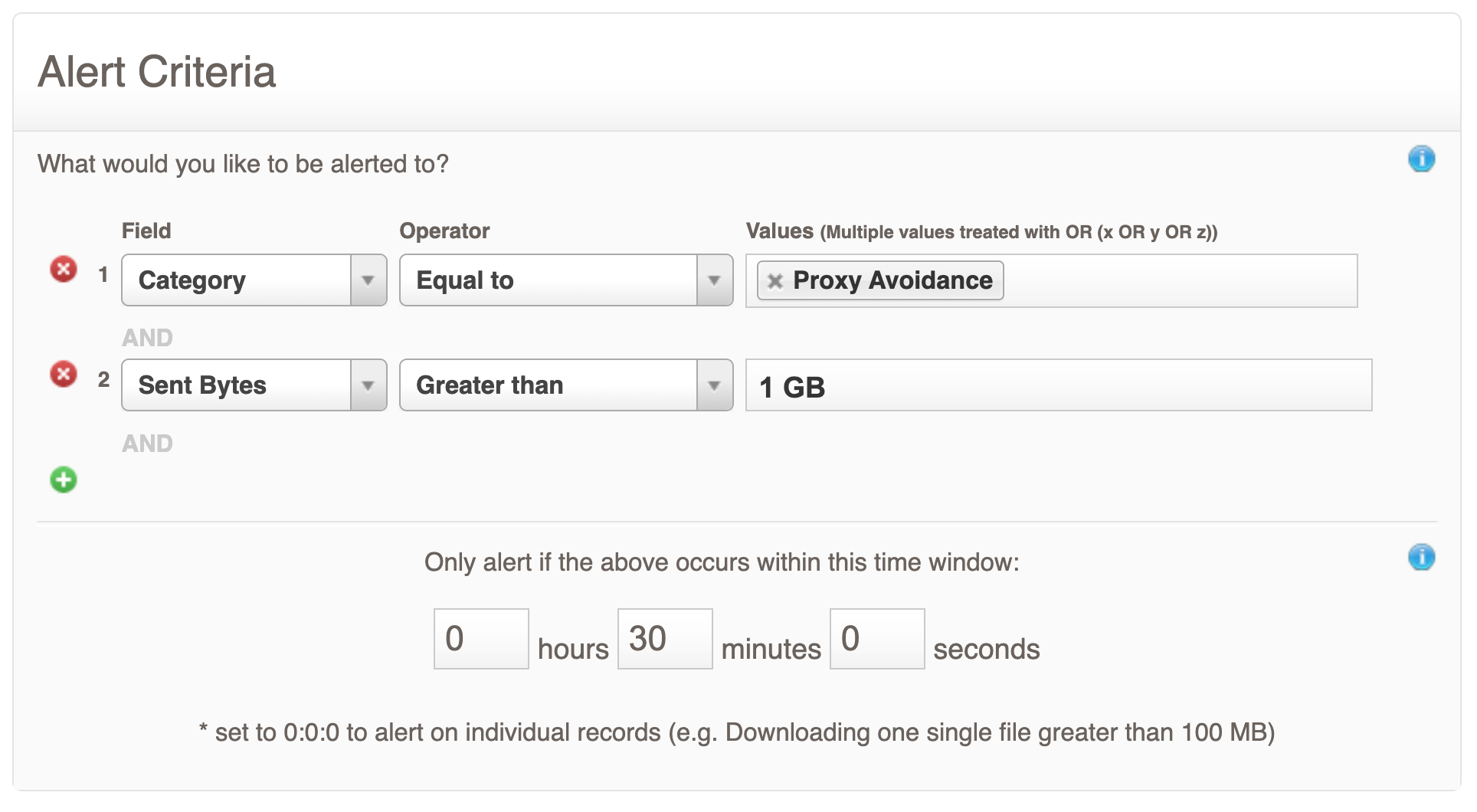
Protect your critical assets
Protecting sensitive information starts with identifying and prioritizing critical data. Organizations should:
Define their most valuable assets, including customer data, intellectual property, and strategic plans.
Implement strict access controls to ensure only authorized personnel can access sensitive systems.
Regularly evaluate protections to guard against malicious insiders and potential insider attacks.
Establish baselines for standard user behavior
To detect what indicates abnormal behavior, organizations must first establish baselines for normal behavior and how anomalies will be dealt with. This may involve:
Assigning risk scores to activities, such as unusual login attempts or downloading of sensitive files.
Flagging anomalies based on deviations from now-established typical user behavior patterns
Investigating alerts to prevent insider threat incidents before they escalate
Enforce policies and security measures
Clear security policies are crucial to preventing insider risks. Steps include:
Defining and training employees in acceptable behavior related to data usage and access.
Educating employees on the importance of compliance with security protocols.
Reviewing adherence to policies and addressing violations.
Insider threat management: Striking the right balance
When signs of insider risks emerge—such as unusual login behavior patterns, unexplained data transfers, or attempts to bypass security controls— you need the ability to respond swiftly. With its user-friendly interface, Fastvue Reporter allows IT teams to analyze firewall data and quickly generate actionable reports, uncovering patterns and pinpointing potential threats. Unlike some employee monitoring tools that cross the line into surveillance, Fastvue equips organizations with the ability to detect and address risks effectively without compromising employee trust or fostering a culture of suspicion. By combining real-time visibility with policy enforcement and staff training, organizations can protect their critical data while maintaining a respectful and secure workplace.
Join top organizations using Fastvue Reporter
Download Fastvue Reporter now and try it free for 14 days or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn