From Insights to Impact: The Transformative Power of User Activity Monitoring
by

Bec May
User activity monitoring (UAM) solutions tend to get a bad rap. People often mistakenly associate them with Big-Brother-like surveillance, or their mind turns to high-profile cases such as the Wells Fargo mouse jiggler scandal that don't reflect how most modern organizations are using these tools. The truth is, it's not the tools themselves that are to blame here. Rather, as with many technologies, it's how they are implemented and used that causes the problem.
When user activity monitoring solutions are applied thoughtfully, with transparency and clear communication, they become a powerful tool for trust and collaboration, not a harbinger of fear and control. Research shows that with ethically based monitoring practices, organizations can identify suspicious user activity, maintain compliance with data privacy regulations, and safeguard sensitive data.
And it's not just the bigwigs in the C-Suite that benefit here — employees enjoy fairer workload distribution, improved workflows, and a safer, more secure working environment.
What is user activity monitoring?
At its core, user activity monitoring involves using tools and software to track user behavior across networks and applications. The scope of this monitoring largely depends on your organization’s needs, workplace philosophy, and the tools employed. User activity monitoring is applied in diverse settings, including schools and public libraries; however, this article will focus largely on monitoring employee behavior within the corporate sector.
Employee user activity monitoring can include tracking internet usage, application activity, and email communications. While some organizations take this a step further, tracking keystrokes, mouse movement, and even taking random screenshots to oversee remote workers, 76% of employers prefer tools like Fastvue, which focus solely on monitoring web browsing and application use.
When implemented effectively, user activity monitoring systems offer a wide range of benefits that support both individual and organizational success: boosting employee productivity, ensuring compliance with security policies, and protecting sensitive company data.
The Benefits of User Activity Monitoring Software
Compliance with Industry Regulations
For companies operating in highly regulated fields, such as the legal, finance, and healthcare sectors, maintaining compliance with data regulations and privacy is essential to ensure legal adherence, protect sensitive data, and ensure operational continuity. Without the right systems and policies in place, this can be a logistical nightmare. Auditors, who were once solely focused on finances, now scrutinize businesses from top to bottom, demanding robust backups, policies, and procedures to protect operations. Firewalls are a critical part of this security framework, providing a barrier against external threats and controlling network traffic. However, firewalls alone don’t provide the visibility into user activity that organizations need to fully protect their networks and meet auditor demands.
Tracking Data Access and Usage: Monitoring tools can log when and how employees interact with sensitive data, assisting compliance with regulations such as GDPR, HIPAA, ISO 27001, and other sector-specific standards. For instance, monitoring tools can log access to electronic protected health information (ePHI) in healthcare settings, documenting who accessed it and when. Even unintentional HIPAA violations can incur penalties north of $2 million, making it crucial for teams to know if unauthorized users have accessed sensitive data and take the appropriate required steps, such as issuing a breach notification letter to affected patients within 60 days of the incident.
Reporting to auditors: Auditors require clear, documented evidence that an organization is adhering to regulatory standards. User activity monitoring tools like Fastvue can generate automated, audit-ready reports that provide a detailed, transparent record of employee behavior across corporate networks and applications:
Access Logs: Comprehensive activity logs report who accessed sensitive data, the access time, and what actions were performed.
Policy Adherence: User activity monitoring reports can provide proof that employees are using approved applications and following security protocols, such as using encrypted communication channels.
Incident Tracking: Real-time alerts can be configured to flag anomalies, including unauthorized access attempts, evidence of unexpected or suspicious behavior, and unusually high data transfer volumes, demonstrating proactive risk management to auditors, which is a requirement under some laws.
Protecting your company's reputation
It’s no secret that data breaches are among the most damaging threats facing organizations today. In 2024, the global average cost of a data breach reached $4.88 million, marking a 10% increase from the previous year and the highest total ever. And it's not just the financial cost companies need to worry about.
Take, for example, Target who, in 2013, suffered a massive data breach, with cybercriminals stealing 70 million customer records, including the credit card information of over 40 million individuals.
The breach not only caused major financial damage, with the cost to Target estimated at around $200 million in settlements and system upgrades, but also led to a significant loss of customer trust. Shoppers questioned the targets' ability to secure their sensitive information, and the company faced public scrutiny and reputational harm that took years to repair. Your organization's reputation is vital to its success. Once trust is lost, it can be tough to claw it back.
Monitoring tools that track user activity in real-time can help prevent breaches by identifying unusual behavior, such as unauthorized access or suspicious data transfers, before they escalate, playing a vital role in protecting your customer’s data and your company’s brand.
Optimized employee productivity
Nobody wants to be the fun police, but at the end of the day, business is business, time is money, and productivity is what gets the job done. UAM tools can provide insight without oversight into how your team is performing, revealing specific trends such as long browsing times on non-work-specific sites, daily streaming activity, or switching between work-related and social media apps frequently and haphazardly.
This isn’t about tracking users' every move or reprimanding them for poor performance. The reality is that most employees want to feel that their work is valued and they are making a meaningful contribution to the team. And for the occasional worker who is asleep at the wheel (or stuck watching yet another ‘How to survive a Zombie apocalypse’ video on Youtube), UAM tools help managers identify these distractions and refocus attention. Sometimes, the issue might stem from boredom due to a lack of challenge or a misalignment between the employee’s skillset and the tasks they’ve been assigned. The key here is using these insights to create teams that work smarter, not necessarily harder.
Recent data clearly speaks to the productivity benefits of UAM. 81% of employers believe that their employee monitoring software has improved productivity. Employees, too, are starting to understand the positive role these tools can play, with research finding that when the reasoning behind productivity monitoring is clearly communicated, the majority of employees see it as a positive. One of our customers has seen unproductive browsing drop by 20% after implementing Fastvue, without creating a culture shock.
Optimized network performance
User activity monitoring software can be a game changer for IT teams looking to optimize network performance. By identifying bandwidth-hogging users or external network dependencies, organizations can proactively streamline network traffic and prevent costly disruptions. UAM tools provide critical data to inform resource allocation and usage patterns, ensuring business-critical apps receive the resources they need to operate smoothly.
If poor network infrastructure is inherited from previous admins, these tools can also help to pinpoint misconfigurations and highlight vulnerabilities, helping the IT team make data-driven decisions about infrastructure improvements.
One of our customers, a mid-sized manufacturing company, faced significant challenges with network outages caused by broadcast storms. Their setup lacked the visibility needed to determine the root cause, resulting in prolonged downtime and operational frustration. After integrating Fastvue into their tech stack, the IT team was able to trace the issue to a misconfigured IP on their storage area network (SAN), resolving the issue and preventing future outages.
Better workload management and balanced work distribution
Leading companies are flipping the script on the traditional application of user monitoring. Once associated with micromanagement, forward-thinking CEOs are now leveraging these tools to promote balanced workloads and to support employees' mental and physical well-being.
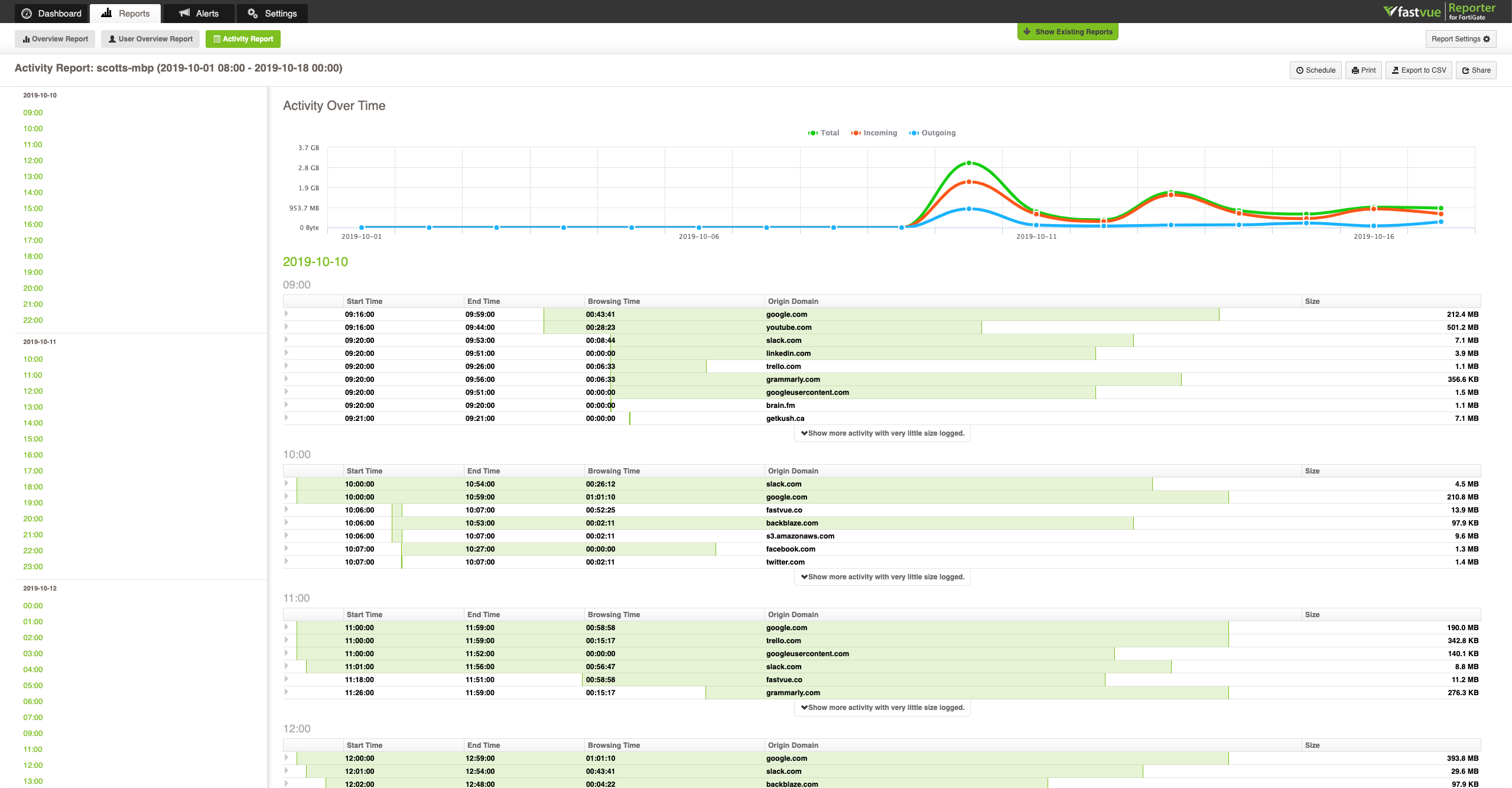
When used in this way, employee activity tracking serves as a powerful tool for promoting fairness and efficiency in the workplace, providing user behavior analytics that can identify workload imbalances, pinpoint areas for improvement, and foster a healthier work environment. With Fastvue, teams can run reports that illuminate user behavior, highlighting workers who consistently work long hours, those who may be overburdened, or those who spend considerable time on unproductive activities and websites, allowing managers to:
Identify and prevent burnout: Ensure tasks are spread evenly, reducing the risk of burnout in overworked employees.
Address productivity gaps: Provide targeted support or training for underperforming employees.
Foster Fairness: Recognise when employees are putting in extra effort and offer incentives or assistance where needed.
Smart monitoring practices are not about control; rather, they are a portal into understanding workplace dynamics, allowing employees to support their teams more effectively.
Streamlining responsibility for productivity tracking
In addition to managing workloads, digital-first organizations face challenges in determining who is accountable for productivity insights. Managers look to HR for answers, who then turn to IT seeking meaningful analysis of raw data such as firewall logs. IT teams loop back to managers, asking if they can provide any insights, and the cycle continues in an overwrought, unproductive loop. Tools like Fastvue eliminate these inefficiencies and frustrations, taking your existing firewall data and transforming it into clear, actionable insights on user activity. With automated reports and user-friendly dashboards, monitoring tools empower stakeholders across HR and individual departments to take ownership of data discovery. Department heads can receive web usage reports for their branch of operations to:
Identify workflow bottlenecks: Pinpoint areas where workloads may be unevenly distributed or where employees may require additional support.
Enhance accountability: Provide transparent performance metrics.
Drive informed decision-making: Enable data-driven adjustments to task allocation and resource planning for greater efficiency.
An evolution in user activity monitoring
Even with all the benefits of user activity monitoring, It’s fair to say that this is never anyone’s favorite job. However, when you need it, you really need it, and the process should be seamless with data you can trust.
The last thing any organization wants is to call out an employee for wasting time on social media only to realize they were accessing legitimate information websites with embedded tracking scripts. That’s where Fastvue makes all the difference. By cleaning up site data and eliminating false positives, it provides accurate, actionable insights, without unnecessary noise.
UAM tools have evolved beyond outdated, intrusive surveillance tools. When implemented thoughtfully, with transparency and ethical consideration, UAM solutions like Fastvue become indispensable in supporting organizational success.
From enhancing productivity and optimizing network performance to ensuring compliance with data protection policies and safeguarding your company's reputation, Fastvue gives organizations the visibility they need, transforming their workplaces into environments that champion collaboration, security, and fairness.
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn

