Deploying Endpoint Protection with Sophos UTM and Enterprise Console
by

Etienne Liebetrau
In this article we will show how to integrate Sophos Endpoint Protection's Web Control module with Sophos UTM using Sophos Enterprise Console (SEC) policies. This method is suitable for large deployments that utilize one or more SECs.
For smaller deployments, please see our other article on how Sophos Endpoint Protection can be completely managed in small environments using Sophos UTM itself.
About Sophos Endpoint Protection
In an environment where you have fixed machines on the network (not traveling laptops) that are never exposed to the Internet directly, Sophos UTM will perform web protection for them. In this situation, adding web control on the endpoint does not provide any additional benefit.
The value of Endpoint Protection comes in when you have mobile users that take their corporate laptop and use them on open Internet connections. Here, Sophos Endpoint Web Control can then apply similar restriction to the users's browsing as they would have while connected to the corporate network. The blocked and allowed sites and categories are the same. Even the block messages are almost identical including your company logo.
Step 1 - Configuring Sophos UTM
Sophos UTM provides the policies that will be used by the endpoints, but it does not actually connect directly to the endpoint. Sophos UTM uploads the relevant policy to Sophos LiveConnect.
To configure Sophos UTM to do this:
- Navigate to Endpoint Protection | Computer management | Global
- Toggle the switch to on
- Select the Advanced Tab
- In the Sophos LiveConnect Registration area, copy the SEC information Hostname and Shared-Key
- Browse to Web Protection | Web Filtering Profiles | + Create New Profile
- Specify a Name for the Profile
- Allowed Network is Sophos Live Connect (The object is auto-created for you)
- Operation Mode is Transparent
- Authentication is None
- HTTPS URL Filtering Only
- Create a new policy without specifying any users (applies to anonymous)
- Filter Action will be the restriction you want to apply to roaming users. Either create a new one, or use an existing one (recommended).
Once the policy has been configured, Sophos UTM will sync the configuration to the Sophos LiveConnect infrastructure. From there it will be retrieved by the endpoints based on the settings they receive from the Sophos Enterprise Console.
Step 2 - Configuring Sophos Enterprise Console (SEC)
The SEC sets the WebControl policy but, in a similar manner to the UTM, it does not actually apply the browsing restriction policy directly. It configures the endpoint to retrieve the policy from Sophos LiveConnect.
Note: These settings will affect the endpoints so I strongly recommend deploying this policy to a test group of users and devices first.
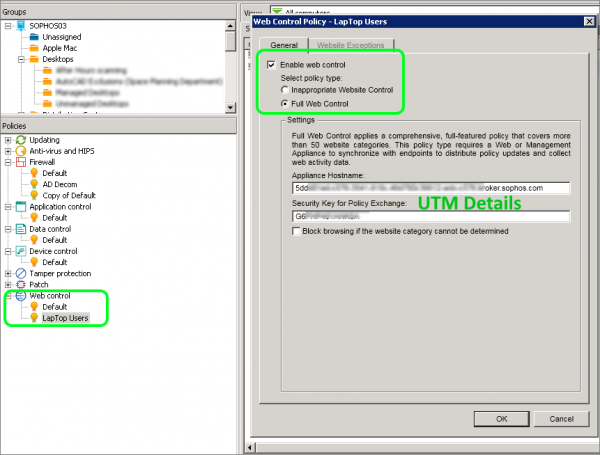
- Open the Sophos Enterprise Console and navigate to Policies | Web Control and Create a new Policy
- Check the the box for Enable Web Control
- Select Full Web Control
- Paste the SEC information Hostname and Shared-Key details that you copied from Sophos UTM earlier
- Click OK to save the changes
- You can now attach this policy to your test group.
- The endpoint policy compliance should change to Awaiting Policy Transfer and then change back to Same as Policy
Step 3 - Test the Endpoint
After the policy update has been received from the client, you can check the policy is being applied correctly.
Note: It can take a while for the client to receive the policy update, as the policies are downloaded from the Sophos Live Connect cloud service. As mentioned earlier the UTM, SEC, and Endpoint never directly share these settings, it is all done via the cloud service. This has a big advantage when it comes to mobile devices that rarely connect to the corporate network.
Checking the Endpoint Policy
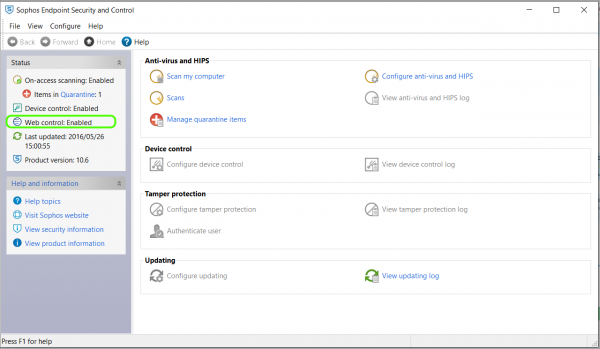
- Open Sophos Endpoint Protect on the client machine
- Web Control should now show as Enabled (This will show up as soon as the policy is applied)
Checking the Web Control Policy
- Check the following folder for files C:\ProgramData\Sophos\Web Control\Policy\
- There should be a number of files in this location. Make sure they are there before continuing to test.
Note: "C:\ProgramData\" is a hidden path in Windows. Type the path above directly into Windows Explorer or the Run dialog, or ensure 'show hidden files and folders' is enabled in Windows Explorer.
Checking browser behaviour
- Disconnect the endpoint from the corporate network and connect it to an open Internet connection
- Open a browser and attempt to browse to sites that would be allowed
- Then attempt to browse to sites that should be blocked
If all goes well, the allowed sites should be accessible and the denied sites should be blocked.
Differences Between On-Premises and Roaming Devices
There are some differences between the Web Control feature that runs on the endpoint, compared to the full Web Protection feature that runs on the UTM.
The following features are not supported in Endpoint Web Control
- Scan HTTPS (SSL) Traffic
- Authentication Mode
- Antivirus/Malware (Sophos Endpoint will always scan, but Dual scan and Max scanning size are not available)
- Active Content Removal
- YouTube for Schools
- Certificate checks
- Streaming settings
- Block un-scannable and encrypted files
- Block by download size
- Allowed target services
- Web Caching
From the user's perspective, everything should seem identical, or at least very similar. Below is an example of the same site being blocked for the user while on the premises and then while roaming.
As you can see the differences are small and unless the user is observant, they may not notice the difference at all.
Keep in mind that as Web Control is enabled for the machine and not the user, you cannot specify different policies for different users. You therefore have a common policy that you apply to all of your devices. If this policy is significantly different from the user's on-premises policy, the user will find that sometimes some sites work and sometimes they do not.
Logging and Reporting of Web Browsing Activity
Having the ability to protect users is great, having the ability to see that the filtering is being applied correctly and that users behave with corporate equipment both in and out of the office is even better!
When connected to the Internet, the Endpoint will log all web traffic activity. The log is uploaded to the live connect service and then retrieved by Sophos UTM.
The log data is stored in the Endpoint Web Protection Log on the UTM. If this is log type is checked in the syslog options, Fastvue Sophos Reporter will analyze this data in addition to the normal Web Protection data, to provide a complete browsing history for users both in and out of the office.
- To add the log source navigate to Logging & Reporting | Log Settings | Remote Syslog Server
- Here you would typically already have the Fastvue Sophos Reporter specified as a destination and the Web Protection logs would be checked. Check the box for Endpoint Web Protection and click Apply.
Note that the web log data for the roaming users gets batched and sent through on a frequent interval. It is not live streaming in the same way it does on-premises.
This may affect the live view in Fastvue Sophos Reporter, but once the data arrives, it will trigger alerts, be inserted into the live dashboards and included in reports as normal.
Unfortunately, the Endpoint Protection log is not as comprehensive as the regular Web Protection log. One of the missing fields is Referrer, which plays a large role in Fastvue's Site Clean feature. At this point in time (UTM firmware 9.403-4), the Site Clean feature will be less effective for Endpoint Protection logs until Sophos update the logging.
Conclusion
Being able to combine the feature sets and implementation of the two Sophos products enables you to not only protect users on site, but also protect them while roaming.
This is done using consistent site definitions, categories and policies to keep machines clean and prevent issues when they connect back to the corporate network. In a split tunnel VPN deployment, this feature is big advantage.
Using Sophos UTM, Sophos Enterprise Console (SEC) and Endpoint Protection makes web filtering a standard. And as we know, standards are great to reduce support and support calls!
Take Fastvue Reporter for a test drive
Download our FREE 14-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How to Accurately Monitor and Improve Sophos UTM CPU Performance
Overcoming Sophos UTM HA Cluster Logging and Reporting Issues