How To Connect Remote Networks with Sophos RED Devices
by

Etienne Liebetrau
One of the very first features of Sophos UTM that grabbed me as a seriously cool feature is the Sophos RED device integration.
The RED or Remote Ethernet Device is a small box you deploy to your remote sites, and it establishes a VPN back to your central Sophos UTM so that anything connected to the RED is seen as part of your network. The concept is not new, but the ease of implementing it, and the elimination of remote side configuration is what makes it really cool.
Once your RED is configured all of your devices on the remote site can be set to browse the Internet through your central UTM. This allows you to have a consistent user security profile across all of your sites. It also means all users, regardless of site can be reported on with the same infrastructure.
What you need
Sophos RED Device
Unfortunately there are no virtual RED devices, so you have to get the hardware. The good thing is that they are relatively inexpensive. There are currently two models. The RED 10 and RED 50. They are purchased as a once off cost with no annual subscription required.
Internet Connection
You also need an Internet break out at your remote site. Anything that can connect to the Internet and provide a DHCP address to the RED device plugged into it will do. This means you can theoretically use any router regardless of the medium such as a DSL, VSAT, T1, T3, ISDN, and 3G.
What is really nice here is that you can switch ISP or even the routers themselves, without needing to reconfigure anything on the RED or the UTM.
Central Sophos UTM
You need a central Sophos UTM that has a fixed public name and/or IP address, and a full guard license. This would typically be located at your head office or data center. To get a fixed public name even from a dynamic connection, read our article on Configuring Dynamic DNS on Sophos UTM.
What you get in the Sophos RED box
The RED devices are design to be both tamper proof and fool proof. There are no buttons or configuration options on the box. The units are all solid-state components with no fans or moving parts and they have a sturdy steel case.
- Indicator LED lights in the front.
- The rear takes the power input.
- WAN port connects to your Internet router
- LAN ports connects to the remote internal network (marked LAN1, LAN2, etc)
**A note on the internal network: ** If your site is small and you only need to connect 4 devices, you can patch them directly into the RED. If however you have multiple devices you can connect them to a standard switch and patch that into the RED. A personal favorite of mine is to extend the connectivity by using a Sophos Wi-Fi AP.
Configure the Sophos RED Device on Sophos UTM
All of the settings for the RED are configured on your central Sophos UTM. That’s right, if you want to change something like DHCP on the remote site, the change is made on the UTM, and the RED simply inherits the configuration.
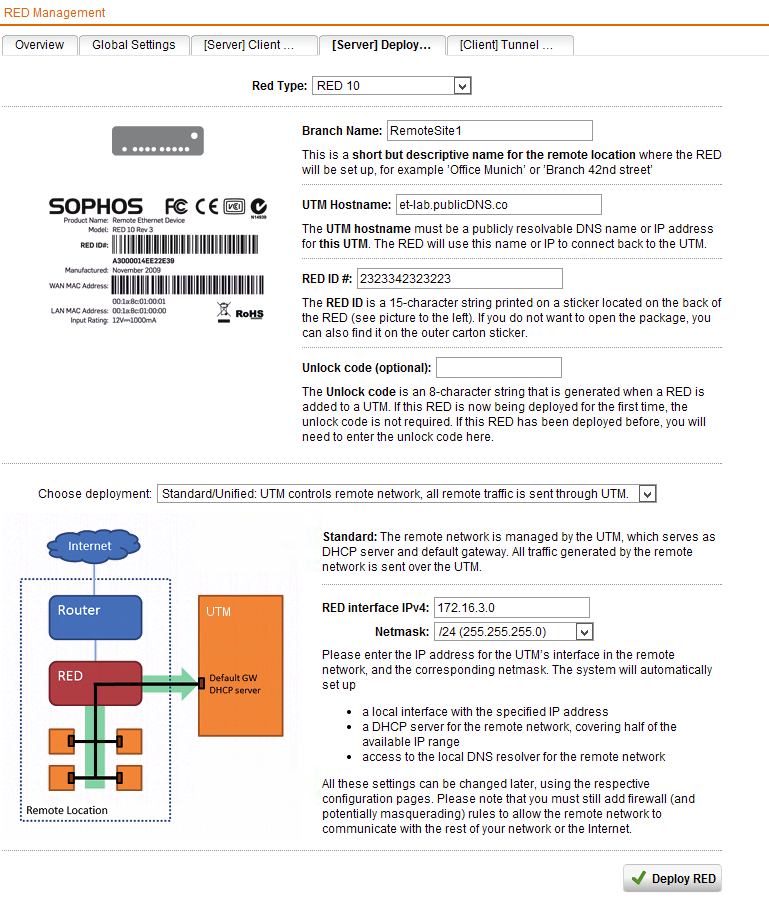
- In the Sophos UTM management console, open the RED Management and enable it if you have not already done so
- Select the Server Deployment Helper tab
- Select the remote device Type (Either RED10 or RED 50)
- Specify a branch name
- UTM hostname is your Central UTM’s public DNS name or fixed public IP address
- The RED ID # is the unique number on the bottom of the RED device
- Unlock code is only require if the RED is re-purposed
- Deployment option is Standard or unified
- RED Interface IPv4 and Netmask is the Network you want to define at the remote site.
- Click Deploy RED
In the background, the configuration you just specified is uploaded to the Sophos provisioning cloud. When your RED device connects to the Internet, it will go to the Sophos cloud, identify itself with its unique RED ID and check for a configuration. It will then download it and configure itself according to the settings.
Add Firewall Rules for the RED Network
The RED device and the endpoint devices connected to it are now able to connect to your Sophos UTM, but not the internal network (yet). The reason is that you have not given the RED network any access to the rest of the private network.
You can be very specific about what you want to allow and deny, but let’s set up a rule where we explicitly trust our remote site and give them access to everything on the internal network.
In the Sophos UTM Web Admin, you will notice an additional interface now exists for the Sophos RED device. There is also a network definition for it auto created by the Sophos RED provisioning.
To grant access to the rest of the network perform the following steps.
- Got to Network Protection | Firewall | + New Rule
- Sources : RED (Network)
- Services: Any
- Destination : Corporate Network
- Action: Allow
- Advanced: Log Traffic
A nice thing here is that any additional REDs that are added later can simply be added to this existing rule. You can, but you do not need to, define separate access rules per site.
Add a Masquerading Rule (if applicable)
If your Sophos UTM is the default gateway for your internal network, everything should be working. If it is not your default gateway, you need to define a masquerading rule. To do this:
- Go to Network Protection | NAT | Masquerading tab | + New Masquerading Rule
- Network : RED (Network)
- Interface : Internal
- Use Address: Primary Address
Connecting to your RED
In my testing, from the time the RED is first powered on, to when the tunnel is up and usable is about 8 minutes. During this time it will update it's firmware and configure itself. Again no actions are taken on the remote site other than having plugged the RED device in.
Subsequent reboots only take about 1-2 minutes before the tunnel up and running again.
When you connect a device to the RED it gets a DHCP address and it has access to the internal network!
You can check on the status of your RED by looking at the Overview tab in RED Management, and open the live log to look further into the actions being performed on the RED.
Conclusion
This has been a very brief introduction to the RED and how to get up and running. They are amazing little devices that allow you to reliably and securely expand you network by adding additional external sites. The fact that they can accommodate almost any Internet connection makes them a key component if you are considering expansion over a heterogeneous WAN.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Sophos RED 10 vs RED 50 - A Detailed Feature Comparison
How to Configure Multiple Site-to-Site SSL VPNs with Sophos UTM